MajorPrivacy
MajorPrivacy is an advanced Windows privacy and security framework integrating kernel-level process isolation, user-controlled code integrity, fine-grained file access policies, and encrypted volume protection.
It provides deterministic control over how software interacts with the system — from process creation and DLL loading to filesystem and network operations — making it one of the most comprehensive user-mode and kernel-mode hybrid isolation systems available for Windows.
Get Started
- Download MajorPrivacy – Compatible with Windows 7 through Windows 11 (x64 and ARM64).
- View on GitHub – Browse the source code, report issues, or contribute to development.
Core Architecture
MajorPrivacy consists of three tightly integrated components:
- KernelIsolator Driver – enforces filesystem, registry, and process-level isolation rules with failsafe mechanisms for system recovery.
- PrivacyAgent Service – facilitates event tracking, handles script evaluation (for rules), manages inter-process communication.
- MajorPrivacy UI – a multithreaded Qt 6-based frontend providing real-time visibility into system activity and security state.
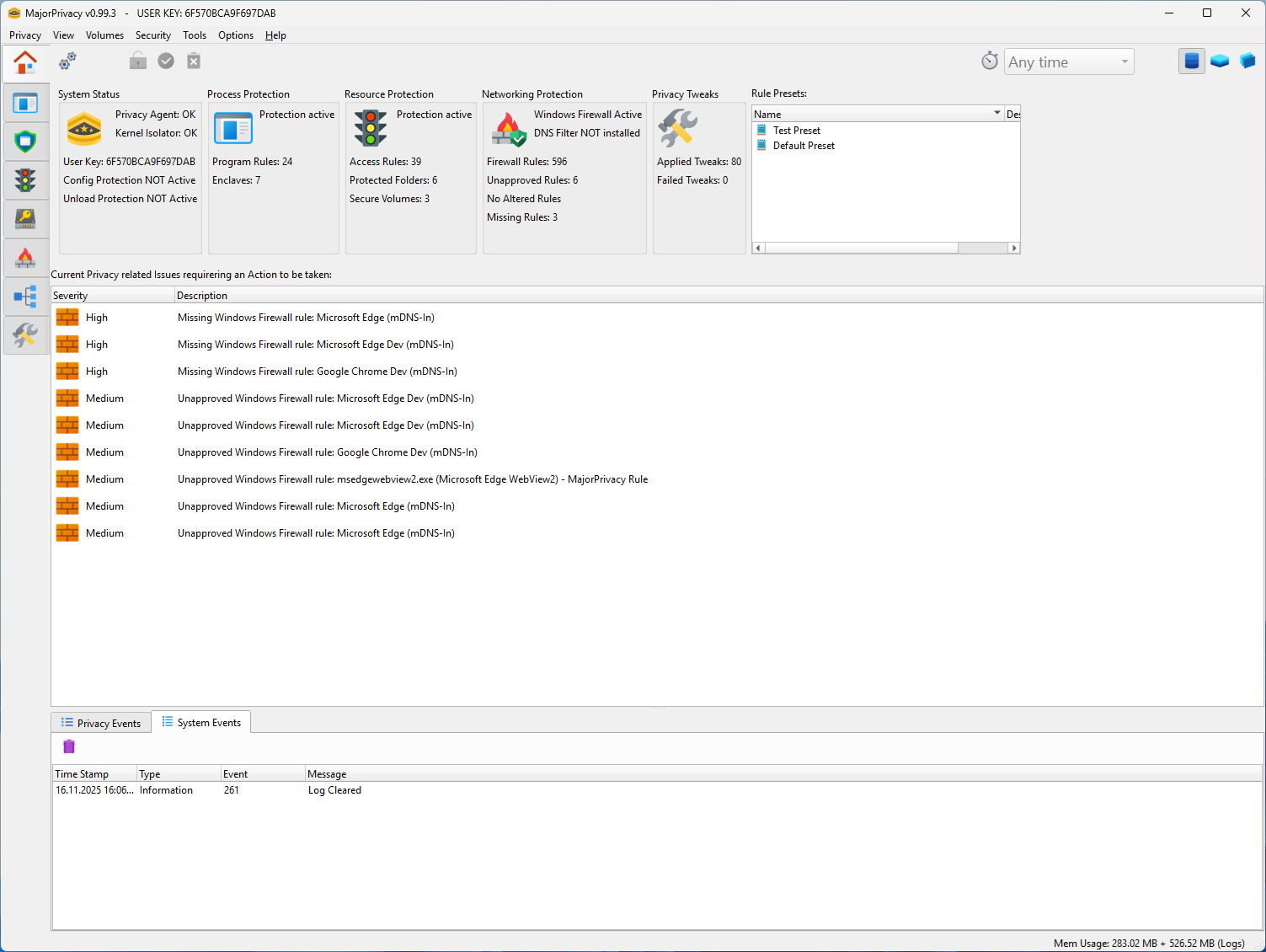
Key Features
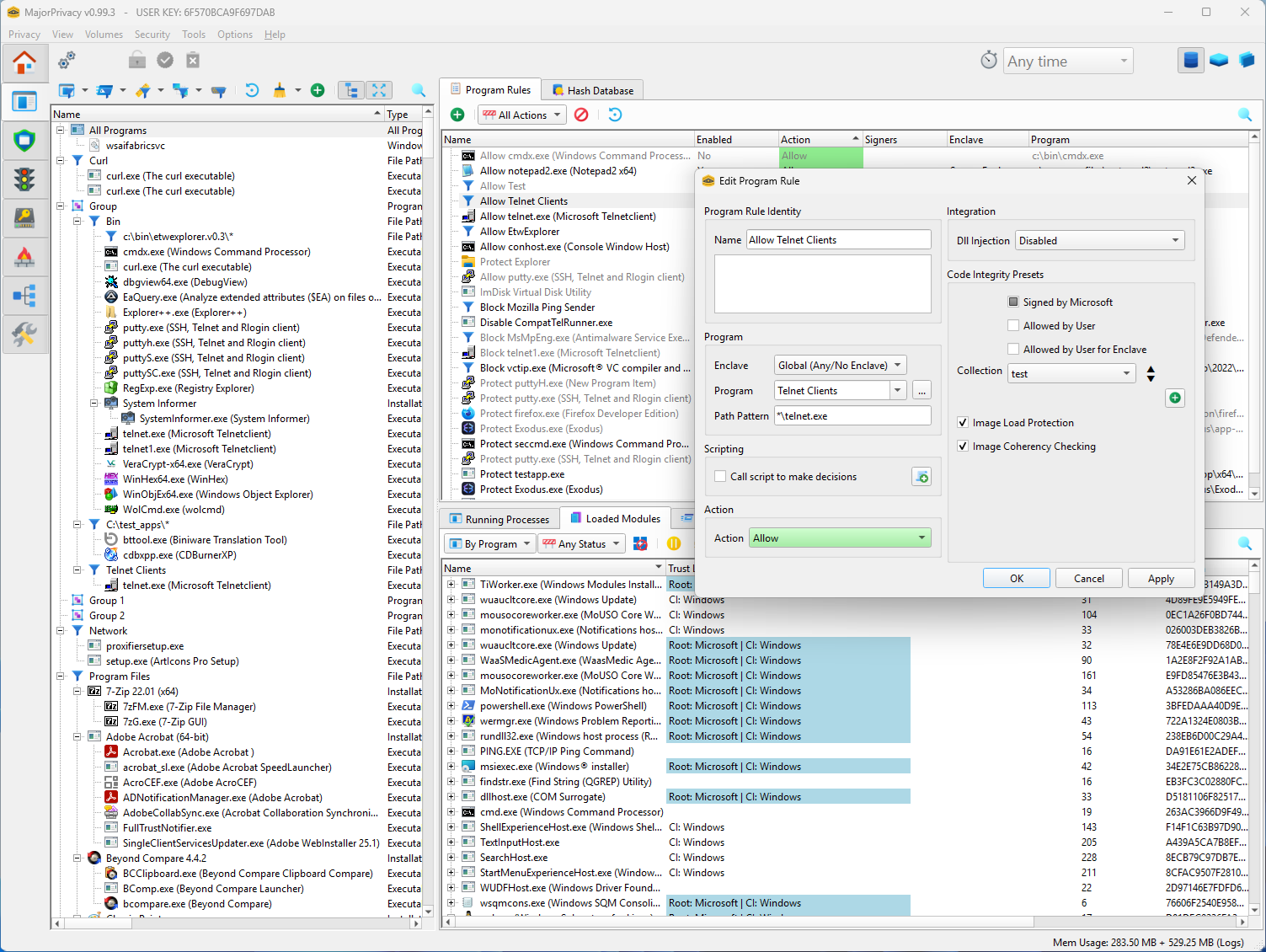
Process & Enclave Isolation
- Run any process inside a secure enclave with strict execution and access rules.
- Inter-process access, DLL injection, and handle duplication are filtered at kernel level.
- Optional token integrity elevation allows enclaves to enforce UIPI isolation of their windows and objects.
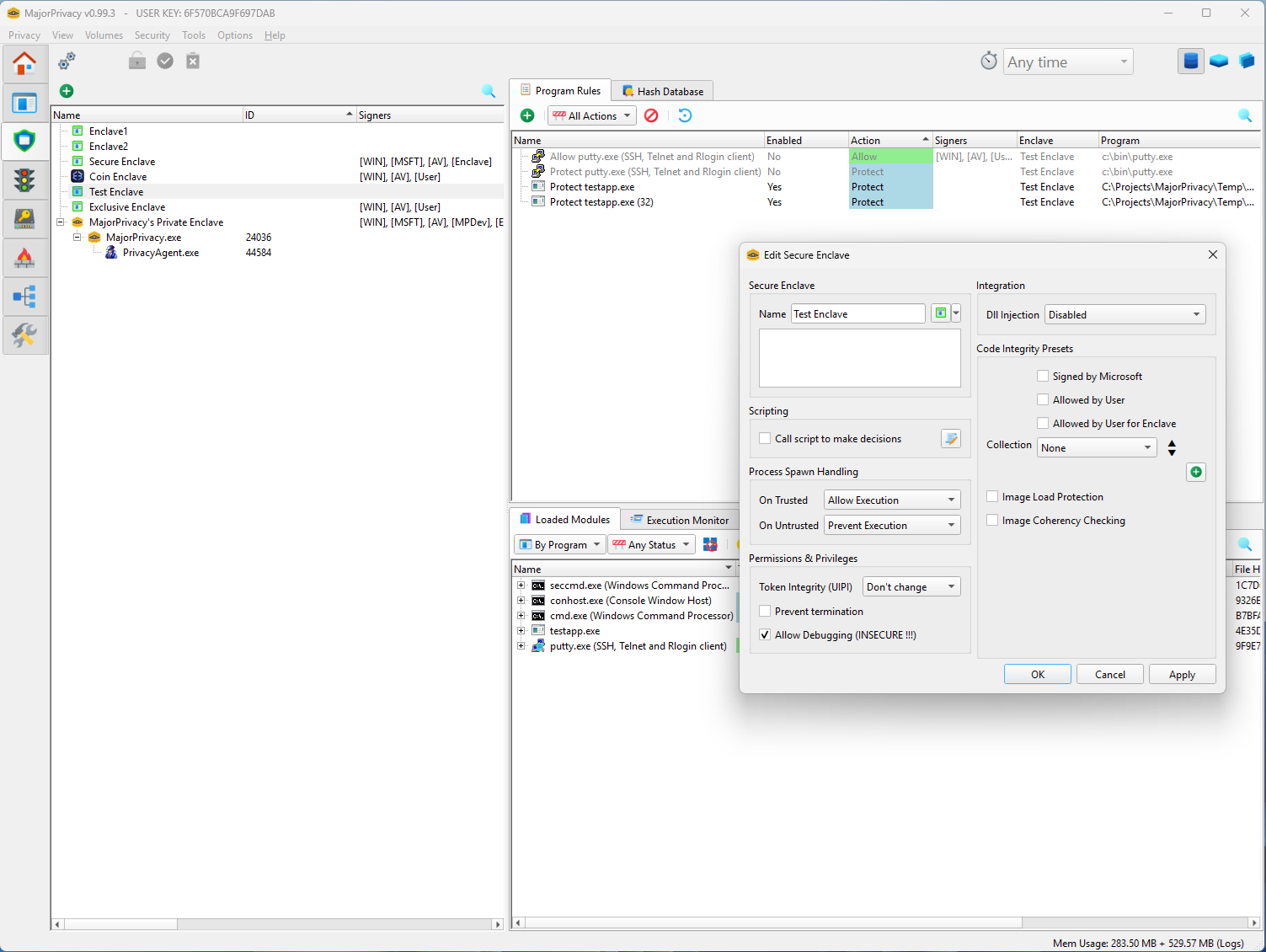
Code Integrity & Signature Control
- Every executable, library, or script can be validated against a user-maintained hash and certificate database.
- User-mode components can be locked to trusted signatures; optionally, users may authorize self-signed binaries compiled locally.
- A UserKey backed Trust System binds trust decisions to registry-stored, cryptographically protected configurations.
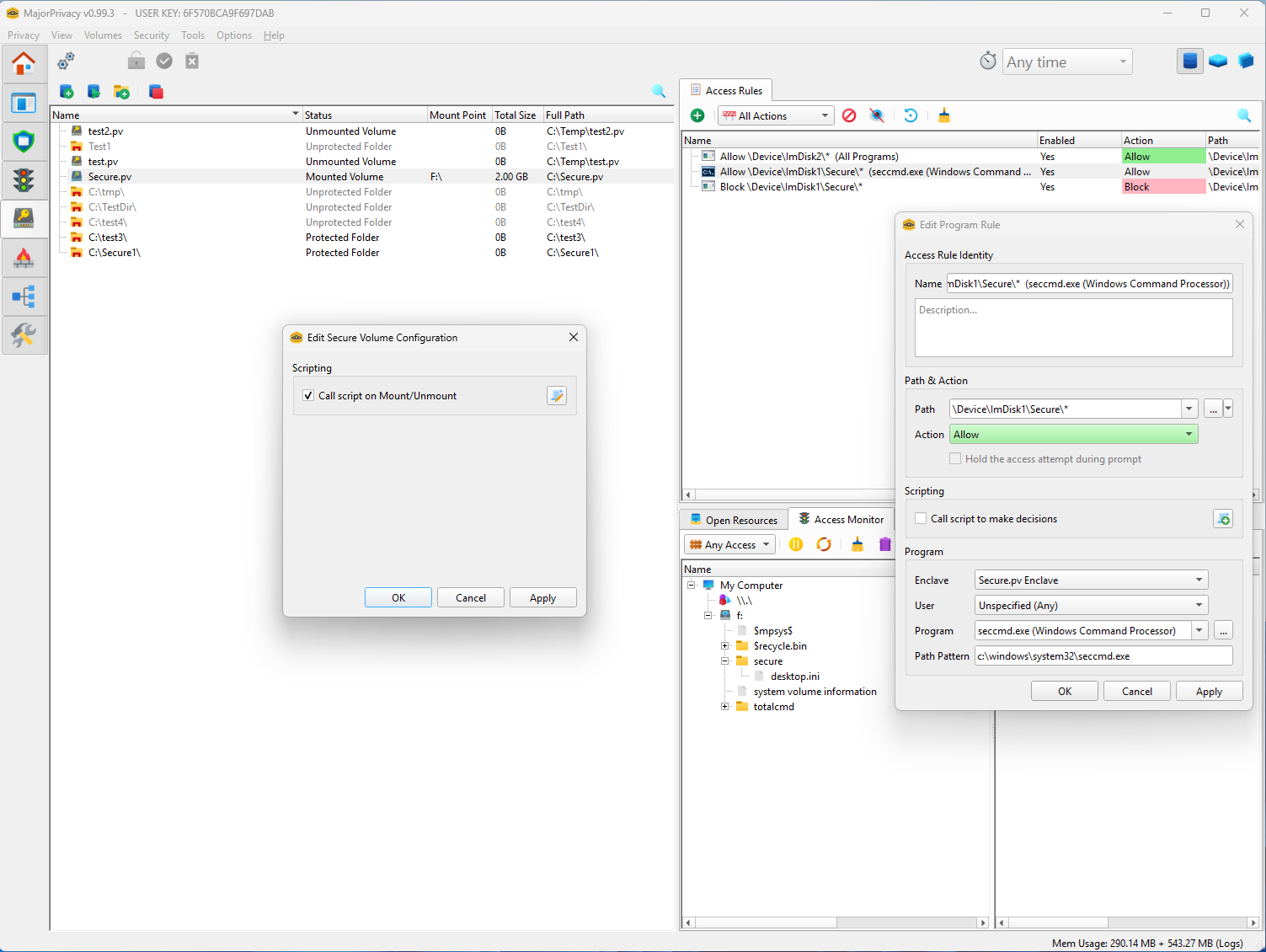
Secure Volumes
- Create encrypted containers with enforced process-based access control: only explicitly authorized programs can open mounted volumes.
- Each volume can host its own rule set and enclave definitions stored in a
$mpsys$file, editable only while the volume is mounted. - Volumes can mount to folders or drive letters and can trigger mount/unmount scripts for automation.
- Hibernation can be disabled automatically while protected volumes are active.
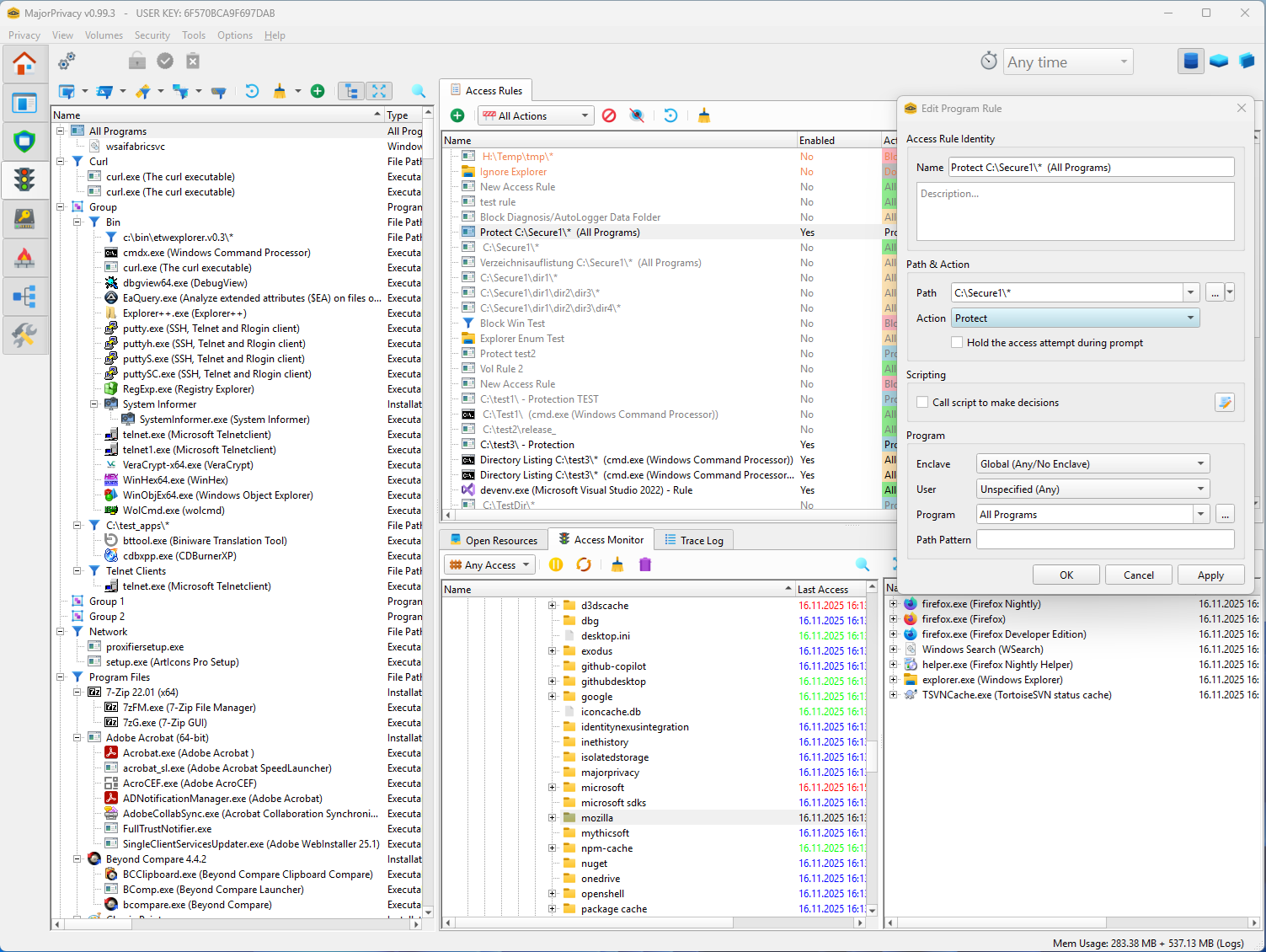
File/Folder Protection
- Define hierarchical rules limiting read/write/execute access to specific resources.
- Access trees and per-program views visualize every operation with timestamp, mask, and status.
- Rules can reference the current user, allowing differentiated access control in multi-user environments.
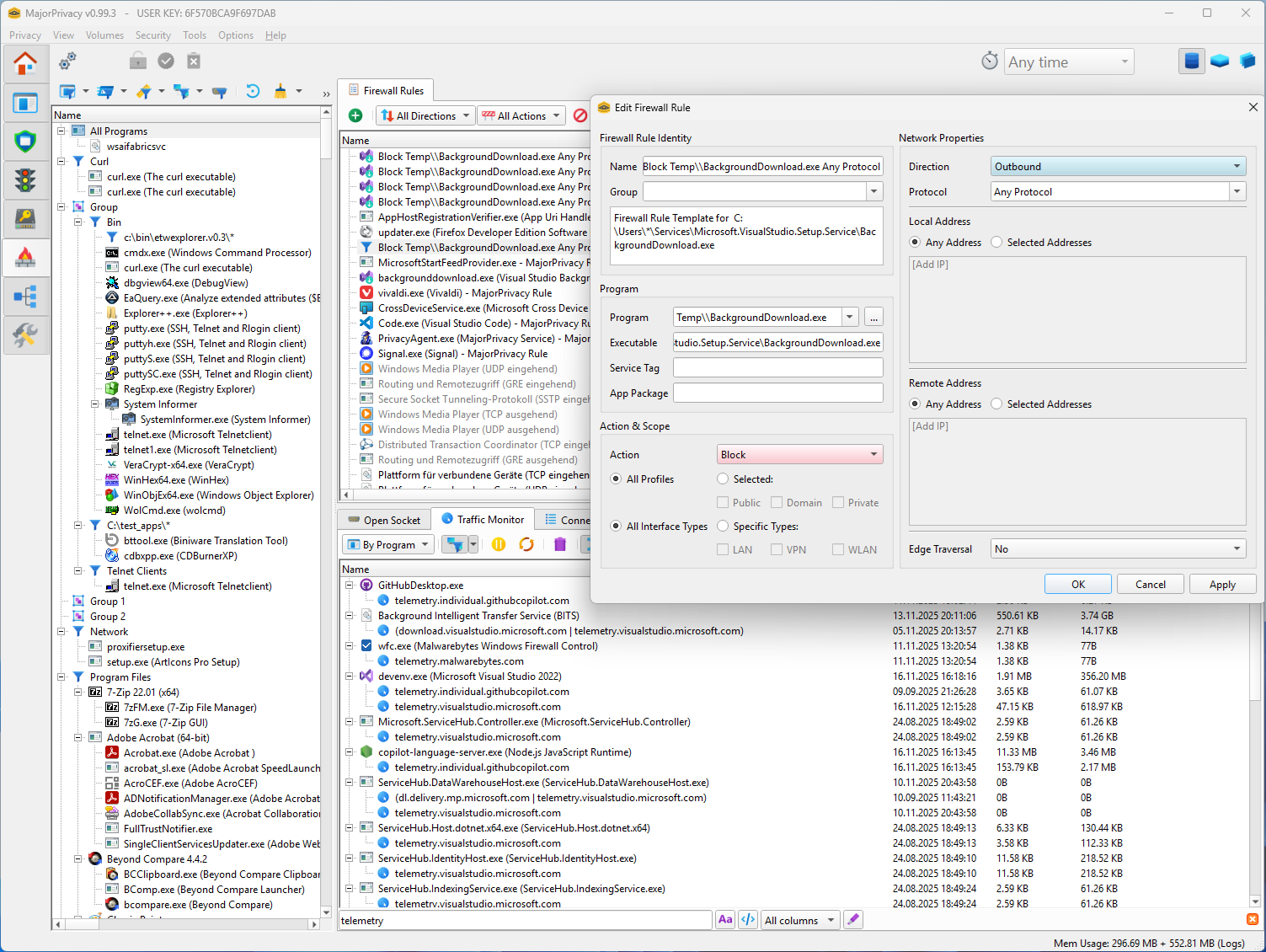
Advanced Firewall Control
- Integrated firewall management and change-detection restore tampered Windows Firewall rules automatically, and create new rules based on templates.
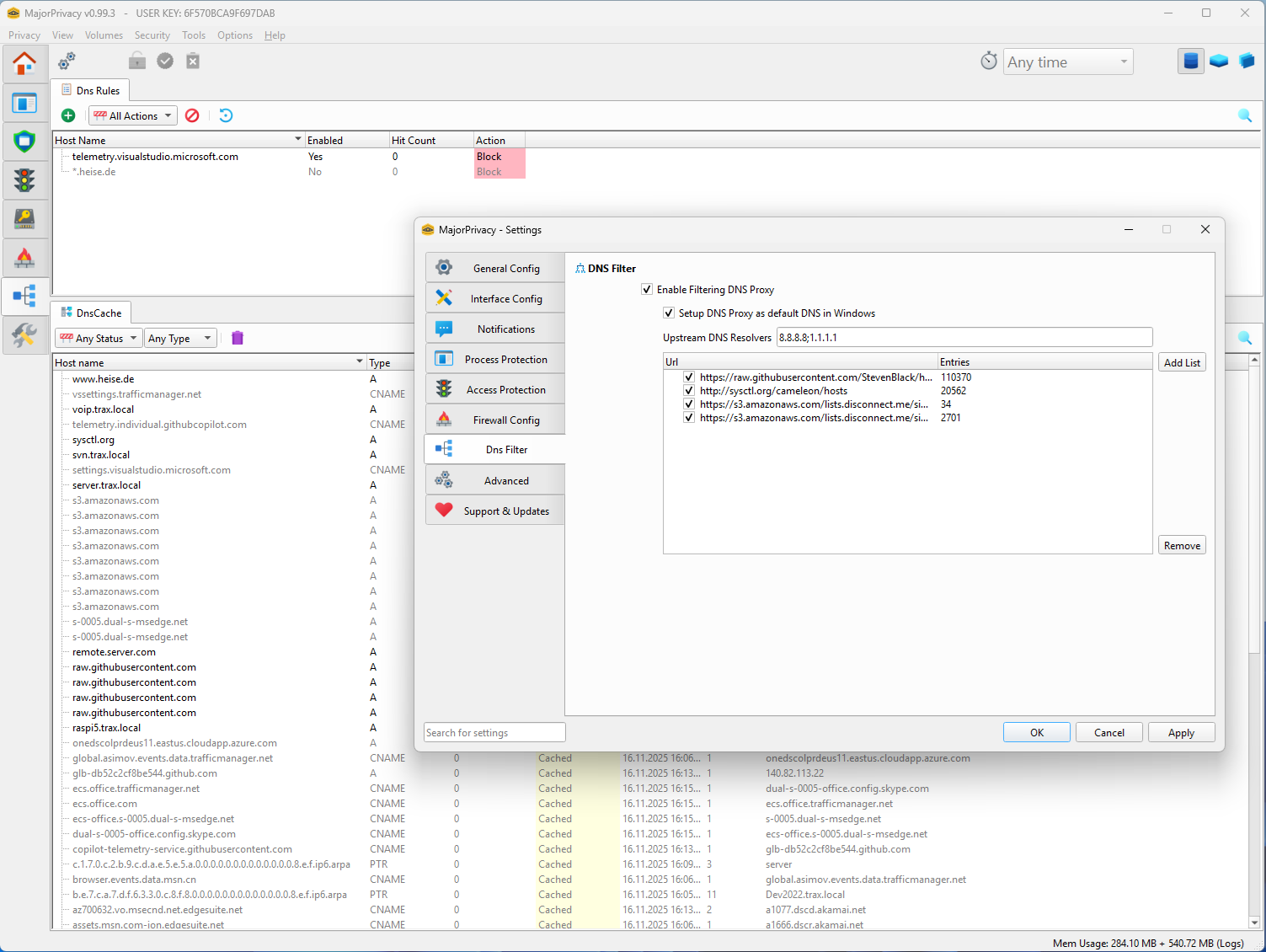
DNS Filtering
- DNS filter compatible with Pi-hole-style blocklists inspects cache entries and maps process-to-domain usage.
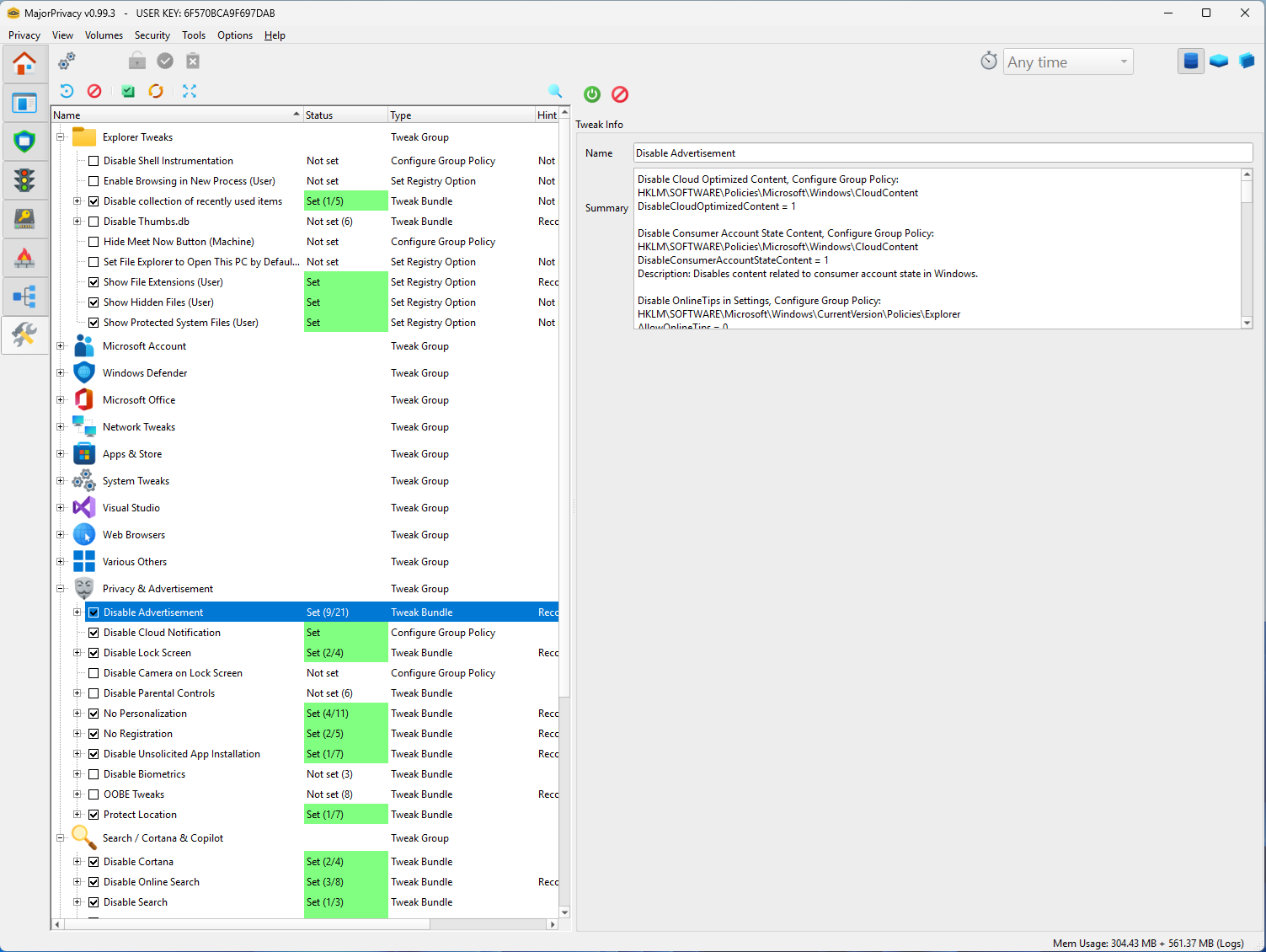
Tweak & Hardening Engine
- Hundreds of Windows privacy and telemetry settings can be toggled and locked.
- Tweaks are stored and monitored, with UI to approve or restore changed configurations.
Diagnostics & Maintenance
- Automated recovery logic for misconfiguration: in Safe Mode the driver automatically suspends enforcement, and after repeated failed boots it reverts to a known-good ruleset or disables itself entirely.
- Diagnostics Information available from the Help menu shows system paths, configuration directories, and driver status.
Philosophy
MajorPrivacy is not a background “security suite” but a user-governed isolation platform.
It empowers technically inclined users and administrators to:
- Define precise, deterministic trust boundaries.
- Inspect and intercept system interactions in real time.
- Secure sensitive data at rest and in use.
- Retain complete control over system integrity without cloud dependencies.
Scriptable Engine
- Embedded JavaScript engine (QuickJS-based) enables programmatic rule decisions and event handlers.
- Integrated editor with syntax highlighting, log window, and runtime error feedback.
Support the Project
MajorPrivacy is a passion project created and maintained by a single developer. If you find it valuable, please consider supporting its ongoing development on Patreon, or through a direct donation. Your support helps ensure the tool continues to evolve with new features and improvements.